Discover, Scan, and Secure
Every API at Scale
Processed
Protected
Increase
API Endpoints
Simplify and secure your API interactions by managing and monitoring your endpoints efficiently.
| ID | API Endpoints | Risk Type | Risk Score | Authentication | Vulnerabilities | Last Seen |
|---|---|---|---|---|---|---|
GET/api/v1/users Payment Service | BOLA | High | OAuth 2.0 | 2 Critical | 2 mins ago |
APIs are being exploited more than everAs the attack surface grows, APIs have become hackers' new favorite hotspots
Increase in breached records in 2024
Of account takeover attacks targeted API endpoints
Of companies face API security problems
APIs are expanding, and so is your attack surface
Look, we get it. API security is tough. Here's what you're up against, and why traditional tools just don't cut it anymore.
Orphan APIs
APIs deployed but not in use - out of sight, out of mind.
Sensitive Data Exposure
One mistake, and your critical data is out there.
API Overload
So many parameters, so many ways in for attackers.
New threats every day
It's like playing whack-a-mole with security threats.
Zombie APIs
Those old, forgotten APIs? Hackers love them.
Shadow APIs
Can't secure APIs you don't know about, right?
Orphan APIs
APIs deployed but not in use - out of sight, out of mind.
Sensitive Data Exposure
One mistake, and your critical data is out there.
API Overload
So many parameters, so many ways in for attackers.
New threats every day
It's like playing whack-a-mole with security threats.
Zombie APIs
Those old, forgotten APIs? Hackers love them.
Shadow APIs
Can't secure APIs you don't know about, right?
Orphan APIs
APIs deployed but not in use - out of sight, out of mind.
Sensitive Data Exposure
One mistake, and your critical data is out there.
API Overload
So many parameters, so many ways in for attackers.
New threats every day
It's like playing whack-a-mole with security threats.
Zombie APIs
Those old, forgotten APIs? Hackers love them.
Shadow APIs
Can't secure APIs you don't know about, right?
The CYBERSEC API Security Platform continuously discovers and scans APIs for 15,000+ vulnerabilities
Discover API endpoints you didn't know existed
Gain continuous visibility into all APIs across your entire infrastructure. Hackers don't limit their search to documented APIs—neither should your security tools.
Detect Zombie APIs
Uncover unmaintained or forgotten APIs which become easy targets.
Reveal Shadow APIs
Identify hidden or undocumented APIs operating without monitoring.
Uncover Orphan APIs
Spot documented APIs handling traffic but unused by applications.
Prevent Data Leakage
Identify APIs handling PII, tokens, and sensitive data without protection.
Secure your APIs with the CYBERSEC API
Security Platform in 5 simple steps
Upload Your OpenAPI Specification
Begin by uploading the OpenAPI spec file for your API. This helps CYBERSEC understand your API's structure, endpoints, and parameters for accurate scanning.
Install a Traffic Connector Integration
Install a connector integration within your infrastructure for enhanced API discovery. This optional step allows CYBERSEC to monitor real-time traffic and uncover API risks.
Continuous API Monitoring
CYBERSEC continuously monitors your infrastructure for any changes in APIs, providing you with complete visibility into your API ecosystem.
API Vulnerability Scanning (DAST)
CYBERSEC performs Dynamic Application Security Testing (DAST) on your APIs, scanning for over 10,000 vulnerabilities, including the OWASP API Top 10 and known CVEs.
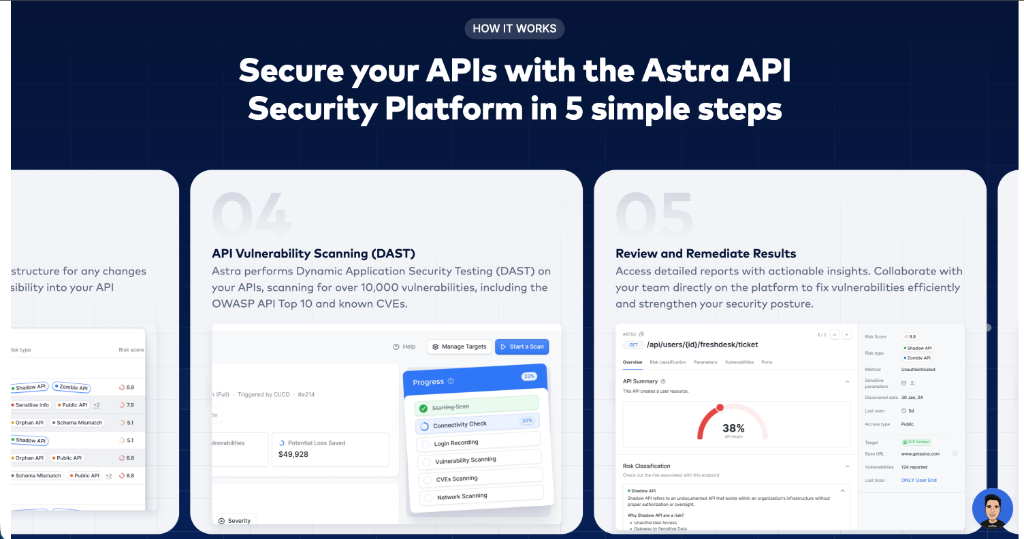
Review and Remediate Results
Access detailed reports with actionable insights. Collaborate with your team directly on the platform to fix vulnerabilities efficiently and strengthen your security posture.
